Back to Top
Mark Jacobs' Technical Speculations Forum
This is chiefly a technical PC/programming area for speculations on the current technological
environment, and some technical problems solved. If you have a PC-orientated problem,
 E-Mail me, and I'll see if I can get a
solution for you. If it's a good one, I'll post it up here, to help other people with similar
problems. Remember, computers can't read your minds, you have to tell them what to do, and
usually, you don't know what you want them to do. After all, a PC is just a few plastic boxes,
and all a programmer's efforts end up as a mere pixelation pattern on a screen somewhere.
E-Mail me, and I'll see if I can get a
solution for you. If it's a good one, I'll post it up here, to help other people with similar
problems. Remember, computers can't read your minds, you have to tell them what to do, and
usually, you don't know what you want them to do. After all, a PC is just a few plastic boxes,
and all a programmer's efforts end up as a mere pixelation pattern on a screen somewhere.
The deterioration of the Borland Delphi and C++ Builder IDEs
by Mark Jacobs - 29/3/2022, 11:26 pm
The discussion below is about the comparison of the 1999 IDE by Borland called BCB5,
and the latest offering of the same IDE by Embarcadero called C++ Builder 11.1.
VSC is a web app editor for the C++ Builder and Delphi environments.
A lot of the problems with the Embarcadero-fuelled emergent IDE can be put down to this :
in the process of the company being sold to other companies, the intellectual impetus is lost,
and memories fade of how the system works deep down.
Code that works consistently is code that is well understood. Without that understanding,
you're left with guesswork.
Security for the Internet of Things Gets More Ridiculous Every Day
by Mark Jacobs - 3/7/2017, 4:39 pm
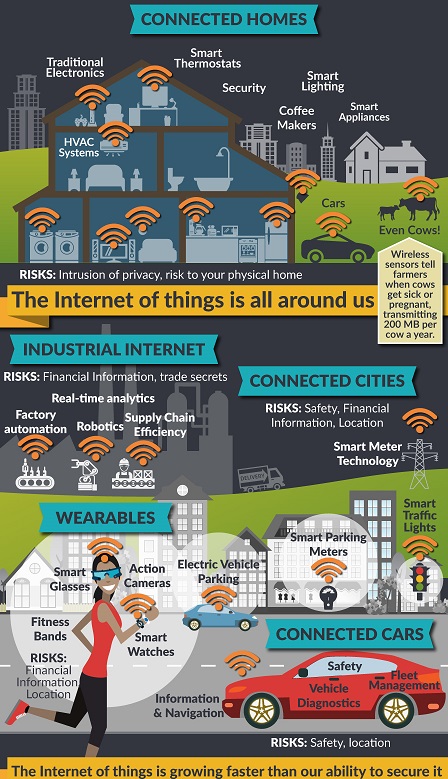
It's a serious, and sometimes life-threatening subject.
Pacemaker hacking
Tripwire
They are using ever more sneaky ways to achieve their ends.
Mirai botnet and security cameras
We Live Security
Vulnerability scan at Incapsula
They do not care who their targets are.
Hospitals resort to paper as ransomware attacks network
Tripwire
But you can see what piques hackers' interests.
Endoscope vibrator hacked
Graham Cluley
I thought, that's enough, but it's spreading like wildfire.
Aga cooker hacked
BitDefender
Car security at risk
Wired
Even second-hand cars
The Register
And then the most hilarious headline I've ever seen (imagine reading this 15 years ago).
Jens Regel of Schneider & Wulf discovered a "web server directory traversal" vulnerability in the Miele Professional PG 8528 dishwasher.
BitDefender
But, then a huge blunder by Samsung, and their proposed/already in use system called Hackers' Playground Tizen, which appears to be in its infancy as far as security is concerned.
Samsung Tizen OS extremely vulnerable
Vice
And, if you think that you're physically safe from attack, don't go to a car wash
Graham Cluley
Someone has to keep an eye on IoT before it becomes chaos. It seems clear to me that the most
important systems for society's infrastructure need to have the tightest and best-deployed
security measures. NHS, ATC, and all sorts of other systems need the finest and most expert
security implementations. However, because of the way these systems are tendered when created,
they end up with the cheapest and most traditional solutions, which are inherently inert and
difficult to change with the times. The people in charge of these tenders (usually public
sector workers under the thumbs of council and other government officials) are some of the
least technically-savvy people on the planet (their kids often know far more than they do about
these matters!). They always fail to realise that the most popular, or most traditional
solutions are very often not the best to deploy, if increased security is what is required.
Systems have to be using the most up-to-date ciphers, transport mechanisms, and DDOS-resilient
hardware and software. This is a full-time job since the security landscape is constantly
changing. That requires a full-time security team working with the systems on a day-to-day
basis. Currently, we have a tender process that gives rise to systems which are often deployed
once, managed intermittently and patched only when things have already gone wrong. Ad-hoc
teams with no previous experience of that particular system, are then employed under incredible
pressure to sort out problems only after the systems have been hacked or have gone wrong. This
cannot continue. The government has to spend LOTS of money on this, or else, one day,
important infrastructures will be brought to their knees permanently.
Windows 10 Spying Techniques and the Ruckus They're Causing
by Mark Jacobs - 26/8/2015, 12:02 pm

Over at
Ars Technica
it is reported that some torrent sites are banning Windows 10 because of its propensity to send
"identifiable to a machine" information to Microsoft headquarters (even bypassing proxies in the process)
which Microsoft, in its own EULA, defines as :-
The data we collect includes:(but is not necessarily limited to)
The software (including drivers and firmware supplied by device manufacturers), installed on the device.
Performance and reliability data, such as how quickly programs respond to input, how many problems you experience with an app or device, or how quickly information is sent or received over a network connection.
App use data for apps that run on Windows (including Microsoft and third party apps), such as how frequently and for how long you use apps, which app features you use most often, how often you use Windows Help and Support, which services you use to sign into apps, and how many folders you typically create on your desktop.
Network and connection data, such as the device's IP address, number of network connections in use, and data about the networks you connect to, such as mobile networks, Bluetooth, and identifiers (BSSID and SSID), connection requirements and speed of Wi-Fi networks you connect to.
One of the comments states, "There should be a opt-out switch. My computers belong to ME not Microsoft. What I do on MY computer is none of Microsoft's business." to which I replied,
In fact, it is the same principle as, "It is my body and I'll do what I like with it.". If I can't excite the naturally-present cannabinoid receptors in my body for the past century because of global laws set up by corporate interests, then why should I be able to encode, with my own algorithms, any film in an arbitrary stream of bits on my computer?
It's a stupid world run by profit, not people.
Anyway, here's a batch file for turning off most of it :-
rem BLOCK WINDOWS 10 TELEMETRY BATCH COMMANDS
reg add HKLM\SOFTWARE\Policies\Microsoft\Windows\DataCollection\ /v AllowTelemetry /t REG_DWORD /d 0 /f
reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\DataCollection\ /v AllowTelemetry /t REG_DWORD /d 0 /f
sc config DiagTrack start=disabled
sc config dmwappushservice start=disabled
sc stop DiagTrack
sc stop dmwappushservice
To remove Windows 7 and 8 updates involving telemetry, use :-
wusa /uninstall /kb:3068708 /quiet /norestart
wusa /uninstall /kb:3022345 /quiet /norestart
wusa /uninstall /kb:3075249 /quiet /norestart
wusa /uninstall /kb:3080149 /quiet /norestart
The Argument Over NSA Spying Rages on in the Light of Snowden and Manning Revelations
by Mark Jacobs - 27/8/2013, 10:04 am
For the super-paranoid among us, the nazis took over the USA after operation Paperclip and they
are now setting up the global fascist superstate for us to be slaves to. My heartfelt thanks
go out to them all!
I really do not care who views what I am doing. Even if they took it to the "Truman Show"
level, I'd still be living my wonderful life, and they'd be stagnant in theirs as they observe
me in full flow. Who cares who's looking at what you're doing? I am not ashamed of anything
that I do - it's all natural!
This isn't that same argument, "if you're not doing anything wrong, then you've got nothing to
hide". This is "as long as what you do, doesn't upset anyone else too much, then go for it!"
and it includes breaking the laws that are made for your own good by strangers who have a
hidden agenda in trying to control your spiritual activities.
So, to recap, spy away, I don't freakin' care! Observers are not participants - they are (and
will always be) superfluous to the machinations of life on this planet. Either take part or
fester!
The Future for the Microsoft Windows Operating System
by Mark Jacobs - 19/6/2013, 12:27 am
Windows-only business models worked until Microsoft could no longer stifle the variety of OSes
better suited to the rising tide of portable devices with "Giga-this or that" processors and
memory. Such processing power made these portable devices extremely desirable and a serious
contender to the Windows laptop. Big players got behind these devices and OSes and they now
seem like they're here to stay.
But, the bigger picture should tell you one thing - these devices and related OSes arrived very
quickly, and will depart very quickly. As the hardware tech moves forward and prices drop,
Microsoft will establish itself in the portable market with Windows-based portable devices, and
the OS will barely have to change as
touch-screens become "proximity aware" and
zoom into what you are trying to target with your stubby fingertip. Such technology has
already been demonstrated at the last CeBit show and featured on an episode of BBC's Click.
This means that the tiny furniture in a Windows OS can remain tiny, and Microsoft can affirm
its presence on touchable portable devices too. In 10 years time, there will be no Android or
iOS challengers. Most will be able to continue using Windows.
All I see is masses jumping frantically onto mad bandwagons and scrabbling around, trying to
offer "multi-platform" support for their development environments, despite this stymieing their
wonderful, and previously, Windows-only product lines. STOP IT! Relax, they'll all come round
and we can continue on the Windows road forever more! 
The Cloud - Have you really assessed the implications?
by Mark Jacobs - 11/3/2013, 10:54 am
In response to a pro-cloud article by Jason Perlow at ZDNet called
Cloud haters: You too will be assimilated,
baggins_z brilliantly stated :-
Computing Power: Your "balls to the walls" mainframe is going to pick up the workload of 100
million plus PCs and deliver the same performance over an internet instead of an eSATA channel
with no noticeable loss in performance? Yeah, right. Put down your crack pipe, the laws of
physics want to have a conversation with you.
Increased Costs: Leasing ALWAYS costs more than outright buying. Do you really think Microsoft
is pushing subscription because they're going to make LESS money at it? Put down your crack
pipe, the laws of economics wants to have a conversation with you.
Security: I just laughed at this one. Here's what you essentially said: Yeah, you're going to
get hacked, but, hey, each time it happens, you'll be less likely to see it happen the next
time. So, just suck it up.
Connectivity: This is where bloggers who write words for a living think their isolated universe
is mainstream. Tell me again how connectivity and bandwidth isn't an issue when I'm a home
user editing my 2 GB home movie.
Your closing arguments demonstrate why the cloud will always be a specialized application. You
are simply arguing for a return to the days of Big Iron. Well, there was a reason big iron
shifted to distributed computing. And it was all economics. When you started shifting large
amounts of bits around, it became cheaper to distribute the computing and data.
Now, tell me in what world the cloud will ever make sense for joe sixpack working on the 12
hours of video he shot during his vacation to the grand canyon. Yeah, he'll upload clips of it
to Facebook (the cloud), but he's not going to store the whole thing on there and work on it
that way.
Your problem is one shared by many technologists. You think the way you work is the way
everyone works.
To me, "cloud" looks like an attempt by corporations to control the software and data your home
computer will be using. Corporations always put profit before technical excellence, whereas a
competent home-user with local data and software, has the opposite intentions. Hence, the
corporation-controlled method is more likely to technically fail than the competent home-user
method. The "cloud" is therefore for dumbed-down users who do not want to take any
responsibility for the computing infrastructure they operate on. More fool them! I have always
believed that if you want your systems working properly then either you take care of them
yourself competently, or you hire someone else to do it. Either way, technical excellence is
what keeps it working, and certainly not profit motives. If a corporation is running
both your software and data in a cloud, and they spy a way of cutting costs by cutting some
corners, they'll do it first, and then judge the consequences of their actions after the
threatened law-suits come in! If you decide to use a business' cloud resources, eventually
you will suffer from that business' greed.
The Browser Wars Hot Up
by Mark Jacobs - 12/10/2010, 10:00 am
1) IE has the best Print Preview function of all the browsers so far. There is nothing to touch
it. Opera forum users have been complaining for years about the crappy print preview function
Opera sports - you can't even scroll fully down to the bottom of the preview window with the
arrow keys! Every new Opera release never seems to address the reported problems with Print
Preview. Firefox has an inaccurate (grossly sometimes) Print Preview function and cannot fit as
much on a page (even with the "Shrink to Fit" setting) as IE. Chrome and ALL of its add-ons,
does not have any Print Preview functionality whatsoever!
2) IE has the worst standards support of all browsers, even with IE8. It is very frustrating
having to write web pages with an eye on IE's quirkiness.
3) IE does "transitions" - a feature I have found very popular with a lot of my user base. None
of the other browsers support page transitions as in :-
<META HTTP-EQUIV="PAGE-ENTER" CONTENT="REVEALTRANS(DURATION=1,TRANSITION=23)">
<META HTTP-EQUIV="PAGE-EXIT" CONTENT="REVEALTRANS(DURATION=1,TRANSITION=23)"> somewhere
in the <HEAD> section.
4) IE9 has definitely not gone far enough to redress the gap between IE and the rest of the
browser world.
5) All other browsers are notably faster than IE at rendering pages once loaded.
6) Debugging JavaScript is a lot easier when you can "Inspect Element". Only Chrome and Opera
support this. Opera's Dragonfly debugging IDE is excellent, although still buggy. Chrome's
"View Source" function re-gets the page from the server, which often means you are looking at a
login page source rather than the page you are actually on with its internal session data
maintained! Having Opera's "Show Error Console" ticked means you get to see how badly coded the
web is out there! Errors even on google's home page sometimes!
7) If you delve into a typical web page, you'll see in Opera's Dragonfly, that most of time
spent rendering the page is often awaiting cross-site syndicated ad servers or stats servers to
respond! Jeez! Thank God for Firefox's AdBlock and FlashBlock add-ons - I use them all the
time when I use Firefox.
The world is still waiting for the "perfect" browser and nobody so far has come anywhere near
offering us one! Chrome was the closest, but then I found out it sends stats back to Google
intermittently, whatever your settings are! That's enough to make anyone paranoid!
Microsoft XP's Design and the NSA Key (again)
by Mark Jacobs - 6/4/2005, 11:50 pm
In response to a forum posting at Wilders Security Forums :-
Why do you refuse to believe the NSA story? Having seen a lot of Windows registry functioning,
it is obvious to anyone that using a Windows PC leaves tracks of virtually everything all over
the machine. The German MOD could not be expected to trash PCs with such info on them, buried
so deeply in esoteric, difficult-to-access places, and gave up the ghost, writing their own
system instead. What is so implausible about that? Does anyone really know the mechanics of
Windows Update, or XP activation, or any of these on-line activities that happen as part of
running XP? Only internal Microsoft employees who are sworn to secrecy, so we'll never know.
The German MOD had intelligent enough software engineers (and a simpler OS) that they could
reverse engineer at least part of what certain on-line activities were happening, and they
discovered that info was being beamed to somewhere in the States! Now, even if you don't
believe this piece of journalism, one still has to question the imbecilic nature of the
programming structures and pointless journalling undertaken by the XP OS. Security should be as
simple as sandbox-out-of-the-box with modern operating systems, but that is not what we are
seeing. It is almost as if Windows was deliberately designed to be implicitly trusting to all
users.
Even Linux has security issues, but it does not seem to want to talk to the outside world as
eagerly as Windows.
There is no good OS out there - is there?
by Mark Jacobs - 27/5/2003 13:24 pm
What I mean to say is that all commercial and free OS's have some 16-bit code and register
usage somewhere in them. Nowadays, there are few 16-bit processors around. Isn't it about time
a new OS was written that is based on 32-bit (or even 64-bit) architecture, with no backward
support for 16-bit whatsoever? The hybrid messes that Windows and Linux have become, are no
starting point for new endeavours. We need to design a programmers' OS that makes app dev a
delight and end users inundated with great apps. Let's dooooooooooooooo it!!!
To make it really clever, we could treat all peripherals as devices which we can read and
write. This would include the memory of the machine, the internet, screen, printers ...
whatever. If it exists outside of the processor, then it is a peripheral and needs a level of
indirection. This will keep the OS adaptable, yet retaining simplicity.
During development, we must put all workers into a huge and impenetrable ivory tower, so that
commercial interests cannot sway, influence or jitter-bug the development processes. MS IBM
Intel Mac Unix Linux and anyone you can think of, will all have to keep their big noses out
until it is finished. They will have no say in what goes into our end product, because they
are only money-motivated. Our team will be technical-proficiency-motivated, and will be
building a computing platform for the future of the human race - one that is very reliable
and solid, but really easy to program. Money just doesn't come into it. Computers are too
important now, for commercial interests to effect development quality.
And, please, the hacks out there, don't come back with glib statements like "Money influences
everything". We have got to grow out of that atavistic way of thinking fast, if this species is
going to survive the next few centuries. Instead of spending trillions on "defence" when
they've got enough "defence" to blow the world up thousands of times over, let's spend it on
our grandchildren's future. Otherwise, society will continue on, unevolving, as it has been for
the past few thousand years - an iniquitous mess (3rd world poverty is unnecessary) consisting
of docile inhabitants with vicious minds (on the whole), policed by dangerously-armed
brainless morons who do what they are told because they are "paid", despite it tweaking their
consciences.
Microsoft's Direction
A brilliant article by Joel Spolsky called "How Microsoft Lost the API War"
Nanobot Danger
by Mark Jacobs - 27/5/2003 13:24 pm
The best website I have seen on nanobot technology is
Ray Kurzweil's.
I once asked a straight-laced nurse whether she would consider injecting heroin. She said no.
I then asked whether she would drop LSD and trip. She said no. I then asked whether she would
inject nanobots that would interfere with her brain to produce a dream-like state where she
could have waking dreams and visions. She said yes! I asked why. She said it would be a legal
escape from mundane reality.
The danger I am trying to point out here is that people will trust government scientists too
willingly, despite the fact that very few of them have shown any ethical grounding in the
past. If a nanobot should "GPF" in her brain, what would the outcome be, and who would be
responsible? If nanobots ever became so common-place as to leak into the atmosphere, then no
one could escape their inhalation. If nanobots ever became so interconnected globally as to
develop an artificial intelligence (cf. very small Terminators), would they regard human
beings as no longer necessary for their development, and in fact kill us off for hogging
precious Earth resources!?!
I disagree with the direction of modern scientific research. We should not be tampering with
genes, creating nanobots which are too small to control, force-feeding the world population
with GM foods, despite no long-term research into their side-effects, and trying to discover
new ways of augmenting the human body and mind with electronics to try to improve life's
experience for everyone. We should be shaping the environment in more natural ways, and not
with a goal of a push-button existence because that sells, but making life more challenging
and not so straight-forward. People in the Western world are becoming zombies - there are no
longer intellectual debates going on in the shopping malls, and TV and pubs have ruined
people's imaginations. It's time to become more natural and lead a more dangerous life with
more challenges. We have to learn to satisfy our instincts as small groups rather than
individually. Families are good; solitary existence in a flat with promiscuous sex is bad.
For the first time in history, there are less married people than single! Technology is
leading us the wrong way.
Why does software seem to get worse as time goes on?
by Mark Jacobs - 3/2/2003 9:37:33 pm
As a computer programmer, I use a lot of different types of software, and brand allegiance
becomes second nature after a while. Nowadays, I just write and use my own utilities for
everything, except browsing newsgroups, mirroring websites, and playing internet media
streams. Under Windows, I have written a media player, an editor and word processor, a file
manager, a database maintenance system, an e-mail client, an image viewer and magnifier, a
graph plotter, a font previewer and calculator, a simple browser to wrap IE's built-in
functionality, a PC clock synchroniser, and a few other bits and bobs - simply because
necessity is the mother of invention. The software industry nowadays seems fat and bloated on
features I don't personally use. How many home users are heavily into XML, Java programming,
and .Net stuff? These are more for business use, not the home user who wants as much
functionality out of their box as possible. I am not saying that their products are useless,
but that they take too long to load, are very full of bugs, and all too often disappoint
rather than impress when used in anger. With custom-made solutions, the opposite is true. I
get just what I need, they're fast and reliable, they always work in anger, and they seem to
scale up far further than the purchasable equivalents. However, I digress.
I have seen some of my favourite software get stuffed with more features, but cope less
adequately with large projects. For example, Opera browser is now in version 7, and it takes
ever longer to load, and crashes more often. The best version was 5. I have seen Internet
Explorer 6 create havoc with my PC, where 5.5 never had any problems. The best version was 3.
Windows Media Player (an absolute essential on any PC) lost track of its purpose when it hit
version 7 and beyond. At this point it became a monster and lost its ease of use and plain
veneer that made it a desktop joy instead of a hog. It also didn't work as well or as fast!
The best version was 6.4. Winamp limped out similarly when it went from version 2 to 3. Real
player used to be a very welcome addition to the capabilities of my PC until it hit version 7
and beyond (version 8 and the current one really suck!). Now I do not use Real Player and I
hate websites that encode .ra .ram and .rm files without the infinitely preferable .wmv and
.m3u Media Player formats. This is because, despite uninstalling their Real Events add-on
package, it insisted on remaining resident somehow. Every hour it would attempt to go out on
the internet to look up crap I'd never be interested in (middle of the road shite whereas
I'm into very obscure stuff indeed). This is without the Real Player portion loaded
in my system tray, so where it resided, I do not know. I won't have stuff like that on my PC,
especially when it takes so long to load anything up, it makes you think the FBI have begun
spying on your interests! Even Quake 3 PR 1.32 has been attacked with the Punkbuster client,
forcing any serious network player to install this buggy, hacked up crap, that introduces
massive amounts of spyware to your PC, for the purpose of excluding cheats from the arenas. I
stuck proudly and fiercely to version 1.31, and still have great fun online. With hundreds of
servers still running the older 1.31 version of Quake 3, it is obvious I am not the only one
who resents the buggy intrusion into our normally reliable world of Quake gaming.
Software is getting larger and more unfathomable than ever before. No brand is exempt. Has
Microsoft got something to do with this. Are they forcing all software industry players to
pump their code full of tracking devices, spyware, and back doors? Is the competition to
attract new customers (or retain old) so strong that software reliability and useability
are to be overlooked in favour of features? Solution :-
Contact me,
and I'll write it expressly for you.
German armed forces ban MS software, citing NSA snooping
By: John Lettice - 17/03/2001 at 18:59 GMT
(Original at The Register)
Background information :-
Look at the security on this mother-f**ker, slap bang in the middle of
the New Zealand countryside :-

Check the following links (before they're trashed by Big Brother) :-
United States Signals Intelligence Directive (USSID) 18 - 27 July 1993
Echelon - The Bulletin of the Atomic Scientists
Spiegel story (in German)
The German foreign office and Bundeswehr are pulling the plugs on Microsoft software, citing
security concerns, according to the German news magazine Der Spiegel. Spiegel claims that
German security authorities suspect that the US National Security Agency (NSA) has 'back
door' access to Microsoft source code, and can therefore easily read the Federal Republic's
deepest secrets.
The Bundeswehr will no longer use American software (we surmise this includes Larry and
Scott as well) on computers used in sensitive areas. The German foreign office has meanwhile
put plans for videoconferencing with its overseas embassies on hold, for similar reasons.
Under secretary of state Gunter Pleuger is said by Spiegel to have discovered that "for
technical reasons" the satellite service that was to be used was routed via Denver, Colorado.
According to a colleague of Pleuger's this meant that the German foreign services "might as
well hold our conferences directly in Langley." We're not entirely sure whose interesting
video conferencing via satellite service has a vital groundstation in Denver, but we note
that Pleuger seems to have gleaned this information from a presentation held earlier this
month in Berlin by, er, Deutsche Telekom.
Which just happens, along with Siemens, to have picked up the gig. The two companies have
supplanted Microsoft (and anything else American) and will be producing a secure, home-grown
system that the German military can be confident in.
Spiegel Article Synopsis
Subject: raus mikrozoft - 3 Apr 2001 15:16:14 +0200
The German army gets rid of Microsoft
The recent revelations on Level and its infiltration within the European institutions started
to bear their fruits beyond the Rhine. According to information reported by weekly
magazine Der Spiegel, the ministry for the armies and that of the Foreign Affairs would have
banished the Microsoft software because of the serious problems of safety which they pose.
Many testimonies proved that teams of the NSA (arranges American espionage in load of the
Echelon system) worked hand in hand with the developers of Microsoft in order to provide
access to information, even protected, of all the computers functioning under Windows.
At the beginning of the Nineties, before the explosion of the volume of the data
exchanged daily on the planet, the NSA's traditional means of espionage appeared less
effective than in the past. The filter systems could no longer cope
in this ocean of very diverse data. It is on this date that collaboration
between Microsoft and the NSA commenced. The federal agents could thus go and find, thanks to secret
"backdoors", information which interested them, directly on the PC concerned. All the
software intended for export would be thus modified. The European governments knew perhaps
about this established fact for a long time but the Germans were the first to react.
All the Microsoft products will be removed from sensitive stations in the two ministries
concerned: Foreign Affairs and Defence. The head of the German diplomacy also decided to
suspend all the projects of video-conferencing, after the authorities discovered that the data
was being forwarded to Denver, Colorado. The German administration thus called upon two local firms,
Deutsche Telekom and Siemens, to find, as soon as possible, a replacement solution.
(Excuse the translation - MJ)
Birth Pangs of the ADSL Nation
by Mark Jacobs - 16/5/2002 5:05:16 pm
It amazes me that, despite lessons learnt in the past, large businesses like BT still insist
on implementing the cheapest and least technologically suitable solutions for broadband
implementations. When they designed the frameworks that would eventually support the ADSL
rollout, one would have thought that they would have made some attempt at being
backward-compatible with dial-up connections. Surely, they would have designed it so that
installation was easy and quick and hassle-free. Undoubtedly, anyone in their right mind
would have built in loads of room in the technology for future higher speed and alternate
connectivity.
When you design an IT solution for a consumer wish list, you would first state each
important requirement and set about fulfilling it, no matter what the R&D costs. And you
only roll it out when it works!
On every score, BT has behaved exactly like Microsoft with its operating systems - the
products reach the public incomplete and buggy.
As I have always maintained, the larger the company, the worse its products are. It is sad
then that governments only tender challenging IT contracts to large well-known companies,
rather than to small software houses who care about what they produce, because it reflects
on them. This is why there is such a high failure rate in the acceptability of solutions
made by these large companies for public sector IT projects. PR for a small company is the
quality of their merchandise. PR is taken care of by special departments in large companies,
and these departments know very little about the technologies behind their company's
products. Only small businesses really care about their clients' long-term happiness. Large
companies just want a massive client base, with plenty of quick bucks, and perhaps a few
refunds. Time to market really matters to the big company, so its products are rushed out,
not thought out.
My Opinion Remains just my Opinion (but it ain't half true!)
by Mark Jacobs (why is it that techies are softies with their opinions?) - 24/6/2000 5:34:31 pm
I think that big software houses simply cannot put technical excellence before profitability.
Hence, what they churn out is untested, rushed, and badly thought out software, that absolves
itself with the ubiquitous "small print" on the end of the licence agreement that states that
the organisation is not liable for any damage or non-productivity caused by installing and
attempting to use this software. That's like an architect saying that his buildings could
fall down, and kill people, but "don't say I didn't warn you!".
I work as sole employee (apart from my boss) for a software house that has produced software
from which many businesses have grown and are flourishing. My philosophy is that you can
only distribute software that you are 100% confident in, and that has been extensively
tested. I also prefer writing stuff in C and C++ because it is just so much faster than VB,
for example. It is also very much more prone to tell you if memory is being clobbered, so
if you have a bug, you're more likely to see it in a 32-bit Windows C++ program, than in a
VB project, for instance.
I cannot believe that people put up with unreliable hardware and operating system software,
when, only a few years ago, we all had very reliable platforms to work on. Claims that
Windows 2000 is stable are only in comparison with Win 9x and NT products. In use it is
still the same over-ambitious, under-tested, "too many cooks have spoilt the broth" type
of product that Microsoft have got used to providing. Too many features isn't a bad thing,
as long as it is not at the cost of reliability and stability. Microsoft are too big to
concentrate on technical excellence though. They think they can solve the programming
problems by buying in the cream of the programmers in Silicon Valley, but this doesn't
work if they all work on separate parts of a project and are not allowed to discuss parts
of it with each other because of fears of internal secrets being leaked out.
Stick with the small software houses, as only they can provide you with the reassurance that
if something isn't right, they'll fix it quickly for you. You will also get through to them
on the phone within 3 rings, and be talking to the programmer after a single transfer of
your call. This programmer will probably not be under much commercial pressure, so you will
probably get the best technical support you could possibly wish for; and it will be
unhurried and relevant.
This is one area where software houses and shops differ. A big shop can still sell you a
quality product. A big software house just wants the money out of your pockets for what
amounts to feature-rich, bug-ridden chaff.
Mark Jacobs warns about Windows XP's lax security.
Background information :-
Find out the fiction about XP raw sockets at
The Register,
or the facts at Steve Gibson's site.
Windows XP will (like Win2000 currently) allow
raw access to the data packets generated
by the home-user's PC, from programs running on that PC. This would make it easier
for hackers to commandeer your machine for nefarious purposes than it is with
Win 9x, Me and NT operating systems. It also allows non-Unix-based programming of
raw socket internet protocols, that is, the home user will have the power to spoof
their IP address, with a bit of API reference knowledge. Most hackers use Unix-based
boxes to stage attacks. Now everyone will be able to. Further background info on :-
1) XP Raw Sockets interview by The Register with Scott Culp,
Microsoft's Security Program Manager.
2) Steve Gibson's analysis of that interview.
3) Steve Gibson's telephone conference with execs and techies from Microsoft.
In an e-mail entitled "XP's deliberate lack of security" to
Steve Gibson,
Mark Jacobs wrote :-
I am a software developer in the UK, and use Windows platforms extensively,
but usually the 9x versions. I have 2 points to make.
Since both are rather speculative, they should be taken with a pinch of salt,
but things really start to fall into place if the 2nd one is true.
1) If the world went hacker-mad because of Windows XP,
then everyone would know who was a bad programmer, and who was good,
trustworthy and employable. This is because it would be just as easy for you to
look at their drive contents, as it would be for them to hack yours.
However, XP is just so big, that it would be easy to hide a wealth of information
about a person's historical usage of their PC, in their PC. With the built-in
cryptography routines, this information could be buried anywhere. Microsoft
(and their cohorts - see 2nd point) know exactly where this info is stored,
and can now retrieve it over the net anytime they want using raw sockets.
From that point, the evidence they glean could soon put the poor user inside prison
for a very long time (see
Infoworld's article). This perturbs me, as the user could be innocent
if double-spoofing were involved, where the packets are bounced off another zombie PC
which changes the IP address to the unfortunate victim's IP address.
2) We must ask ourselves why Microsoft (which is currently easily pressurised by the Government)
is so intent on having a security-free common base system installed on all PCs in the world.
Certainly, it would afford governments more control over their citizens, and raw sockets is
a standards-based way of achieving this control. By rendering the use of these powerful
Internet research protocols open to all and sundry, government agencies would not require
any special "back doors" or hacks to utilise them for spying and surveillance. The FBI and
NSA are NOT notorious for their technical expertise! So the NSA would not need their
secret NSA cryptography key, for example (search Google for nsakey). The recent decision
not to break up Microsoft may be a direct result of them leaving raw sockets an open
facility in XP. I think the deliberate manner in which Microsoft is ignoring security
issues (and Steve Gibson's highly-prized technical advice) is due to the wolf-like
appetite the governments of developed countries have for secretly spying on their
citizens, and the pressures they can exert on technology-development companies like
Sun and Microsoft. By the time XP is lapped up by consumers everywhere, governments
will have installed consumer control of Orwell's 1984 proportions, whilst the consumers
think they're having a wonderful XPerience. Meanwhile, the hackers are ganging up to wage
war on the new Internet-driven society. Government organisations around the world
are mysteriously insisting on the use of Microsoft software for their new communications
infrastructure (.NET and XP), and it just doesn't seem to make sense in the current climate.
When Mr.Gibson was telephone-conferenced
by Microsoft execs and techies, the image that
came to my mind was that of the faces of these "responsible" people, as the inescapable
logic hit them. If only there was a webcam in their conference room! Many times have I
seen the face that throws logic and common sense to the wind, because of ulterior motives.
The fixed gaze, as if saying, "You just don't see the whole picture, do you?", whilst
I become more and more concerned that it is these kind of people who are running things.
And there was me thinking that to get to that kind of position in life, you have to prove
your technical worth, and your ability to co-ordinate logic and common sense. No, you just
need to know how to act ignorant, be completely bribable, and corruption is a definite plus!
The same goes for all top positions on this God-forsaken planet. We need to change the way
things have become.
 E-Mail me, and I'll see if I can get a
solution for you. If it's a good one, I'll post it up here, to help other people with similar
problems. Remember, computers can't read your minds, you have to tell them what to do, and
usually, you don't know what you want them to do. After all, a PC is just a few plastic boxes,
and all a programmer's efforts end up as a mere pixelation pattern on a screen somewhere.
E-Mail me, and I'll see if I can get a
solution for you. If it's a good one, I'll post it up here, to help other people with similar
problems. Remember, computers can't read your minds, you have to tell them what to do, and
usually, you don't know what you want them to do. After all, a PC is just a few plastic boxes,
and all a programmer's efforts end up as a mere pixelation pattern on a screen somewhere.




